
Security is not a product, but a process. We help you find the gaps.
A security system with several layers is difficult to hack. So, even if your data is targeted, getting through the many tiers of security will be a hassle.
Regulations and standards in information security and cloud computing are complicated. Let us help you implement, maintain, audit and certify compliance with these standards if needs be.
We helped numerous organizations improve their Governance, Risk and Compliance strategies in the Middle East and beyond. Our tailor-made advisory, solutions and training gives organizations the ability to combating against cyber war fare.
Our very own tailor-made service offering CARAT℠ focuses on key areas:
Compliance Advisory (CA): We help our clients navigate through a myriad of international standards and national / regional regulations in the UAE, KSA, EU. Our clients can be rest assured that we can handle assessments, implementations, and audits, as applicable, based on ISO/IEC 27001, ISO/IEC 27017, ISO/IEC 27018, UAE IAR, ADISS, ADHICS, Dubai ISR, NCRMF, GDPR, NCA ECC, NCA CCC, SAMA, NIS2, DORA, etc. Our services include the following:
Risk Analysis (RA): We follow the ISO/IEC 27005 guidelines to assess whether the unique circumstances make a given control applicable or not in the specific setting being analyzed, and help our clients identify security gaps within their organization that impact critical business operations.
Training (T): We help our clients close the skills gap in key areas such as information security, cyber security, cloud security, risk management, compliance management, and business continuity. Our training offerings are flexible and designed to meet a wide range of expectations. We provide both private and public classroom training, as well as virtual instructor-led sessions and online self-paced courses, some of which include recorded video sessions. Learn more…
Here is an example of our services, tailored to the NIS2 and DORA regulations:
We conduct thorough evaluations to identify areas needing improvement in your organization’s compliance posture and provide detailed, actionable recommendations to address gaps and enhance compliance with mandatory regulatory requirements. Once we identify security gaps, we can provide a roadmap for addressing and mitigating unacceptable risks. Furthermore, our team designs and supports your organization in implementing tailored compliance frameworks that meet both DORA and NIS2 requirements.
We ensure that your organization’s controls and processes are optimized for efficiency and effectiveness, leveraging proven security standards and industry best practices. Lastly, we provide handover sessions to equip your team, management, and employees with the necessary insights for maintaining compliance. Our sessions focus on the key aspects of both DORA and NIS 2, ensuring that your staff is well-prepared to effectively manage and mitigate risks.
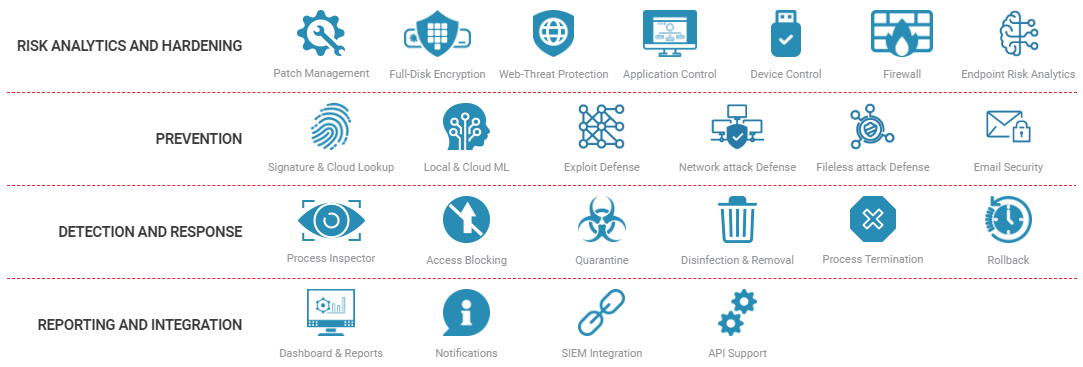
To mitigate technology-related risks, we recommend using Bitdefender GravityZone Security Solutions that offer comprehensive protection for physical and virtual desktops and servers, plus mobile devices and security and antispam for Exchange mailboxes. The antivirus and antimalware come with behavioral monitoring, zero-day threat protection, application control, firewall, device control and content control with anti-phishing and anti-spam for Exchange mail servers. Effectively identifying, assessing and remediating endpoint weaknesses is pivotal in running a healthy security program and reducing organizational risk. Bitdefender Endpoint Risk Analytics is an infrastructure that reduces exposure and hardens the endpoint surface area by discovering and prioritizing risky OS and software misconfigurations. Administrators can now address vulnerabilities using this new interface.
Read in this article how Bitdefender Network Traffic Security Analytics extends protected areas with network based security that blocks threats like Brute Force attacks, Password Stealers, Network Exploits, lateral movements before they can execute. This tool delivers a new level of protection against attacks aiming to gain access to the system by exploiting network vulnerabilities.
All Bitdefender security tolls mentioned above are MANAGED FROM A SINGLE CONSOLE for any type and number of endpoints in any location. LET ME SAY THAT AGAIN: All endpoints are protected – physical, virtual and cloud – no matter the form factor, workstation, server, embedded, mobile, or the OS, Windows, Linux, Mac, by the #1 ranked solution for protection and performance in independent tests!
GravityZone Advanced Business Security is based on a layered next-gen endpoint protection platform that includes endpoint controls, the industry’s best prevention, detection and blocking capabilities using proven machine learning techniques, behavioral analysis and continuous monitoring of running processes, remediation and visibility.







Email continues to be the #1 attacked vector by cybercriminals: as of today, 95% of attacks leverage email. Email attacks are relentless, tactics change rapidly, and sophistication is growing, hence understanding the email security landscape is paramount. If email attacks have been bugging you, we can configure DMARC specification to prevent unauthorized use of your email domain to protect your employees from spam, fraud, and phishing. Furthermore, you will be able to use the DMARC SaaS Platform to see who and what across the Internet is sending email using your email domain.
We advise you to accept that some attacks will breach your defenses – hence you must PLAN for it and be READY. Organizations providing regular information security risk awareness to their users combined with phishing and social engineering campaigns are highly effective in educating their workforce in combating against cyber threats. Particularly phishing and social engineering campaigns helps businesses to address the threat posed by ‘insiders’ who – knowingly or otherwise – may perpetrate or facilitate cyberattacks.
Furthermore, you need to have an effective incident handling process to combat against cyberattacks. It is important to ensure that CSIRT / IRT staff have the skills (if not, check our security fundamentals and in-depth training offering) and resources to quickly identify and isolate problems, determine the level of investigation and response required, and maintain business as usual. Importantly, security measures should make organizations more resilient, and not restrict core business.
Get in touch for a tailored SOC Analyst training that provides knowledge about: architecture, networking, core analyst skill set, common tools and techniques, SIEM log and audit policies, EDR & EPP investigation, network traffic analysis and collecting pcap, malware basic analysis, phishing analysis and indicator extraction, threat intelligence, threat hunting, rule writing, detections frameworks, incident management, incident response, vulnerability management, deployment of open source tools. We have years of experience in these specialist areas where you could put the cyber warfare worries behind you and instead focus on what you are best at.
Disasters happen, recoveries have to be orchestrated. By failing to prepare, you are preparing to fail.
Our Business Continuity and Disaster Recovery advisory services aim to prepare your organisation to maintain ‘business as usual’ in the face of major disruption. Disaster Recovery is an essential element of a resilient organisation, which requires its critical business information to be recovered as quickly and efficiently in order to minimize downtime and keep the business running.
It is our mission to enhance the resilience of UAE’s critical information infrastructure entities by providing public and private organisations with independent, expert advice on all aspects of business continuity and disaster recovery. Cyberstrat expert consultants will:
Perform Business Impact Assessment and gap analysis to examine your most critical business processes and determine what resources are needed, for example, technology, people, suppliers and premises. Our risk-based approach will help you understand your business continuity requirements, ensuring that they identify and cover all critical areas of your business.
Conduct Risk Analysis to identify and measure risks to critical business processes, people, and technology.
Document your continuity strategies and approach in order to prepare your team to recognize threats at an early stage and empower them to take swift action before incidents escalate to crisis.
Build a Business Continuity Plan (BCP) for each business unit that is tailored to your organisation and aligned with your business objectives to ensure that your business quickly returns back to normal.
Set out the Disaster Recovery Plan with strategies allowing your organisation to operate in the aftermath of an incident escalated to crisis, and how it expects to return to ‘business as usual’, and can provide system recovery advice for your critical systems to ensure they have comprehensive disaster recovery plans that can be recovered in line with your requirements.
Present risk-reducing solutions based on international best practice and framework.
Help you with the development, training and testing of comprehensive business continuity plans to provide you with the assurance that the tests for off-site recovery capabilities will be passed and your business can recover as quickly as possible from an incident escalated to crisis.
Provide awareness training tailored to job roles on how to use the software, and relevant aspects of business continuity and disaster recovery tailored to your organisation. This can include specific guidelines to your employees on what they should do once the BCP and DRP have been invoked.
Data is the new oil. Where there is data smoke, there is business fire.
Compliance with data protection laws and regulations is always ongoing. Due to much uncertainty about some of the technicalities of the GDPR regulation, many organisations are still partially compliant and in risk to be fined if found breaching GDPR requirements with fines of €20 million or 4% of annual turnover, whichever is greater. Moreover, when mandated to implement the requirements of multiple data protection laws and regulations, many organisations are finding themselves challenged by the task.
Cyberstrat provides support and advice throughout your journey to GDPR compliance. This begins with data classification framework and implementation, data protection impact assessment, and continues with a gap analysis, identifying areas for attention through data security provision, awareness and staff training. Here are some of the main steps needed to become GDPR-compliant: